Security
Because security matters!
We make sure that everything you store within HOLA system is safe and only accessible by authorized users. HOLA provides powerful security tools that enable granular security setup, temporary access, security inheritance, location restriction and access log.
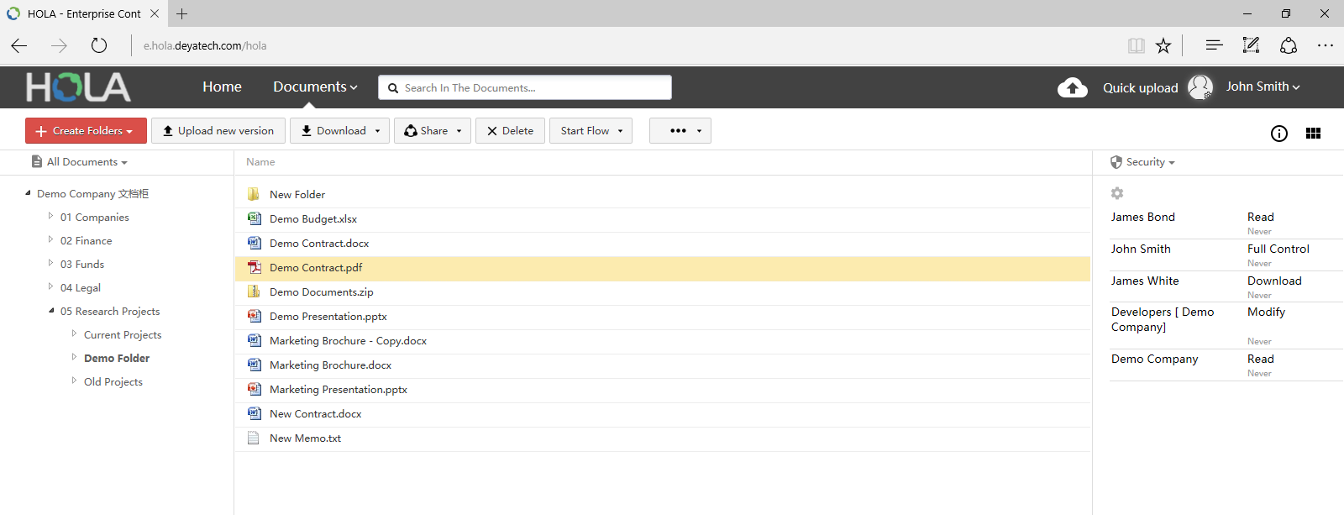
Document & folder security
HOLA provides following pre-defined security settings that can be granulary set on top individual documents or folders:
Security inheritance
Often you need to have the same security for folder as well as all content of the folder (all documents and subfolders inside the folder). HOLA offers a security inheritance feature, where once you setup folder security you can tell HOLA system to enforce such security to content of the folder.
All you need to do is to check a checkbox when setting up folder security. This makes security setup much faster, easier and more convenient.
Temporary access
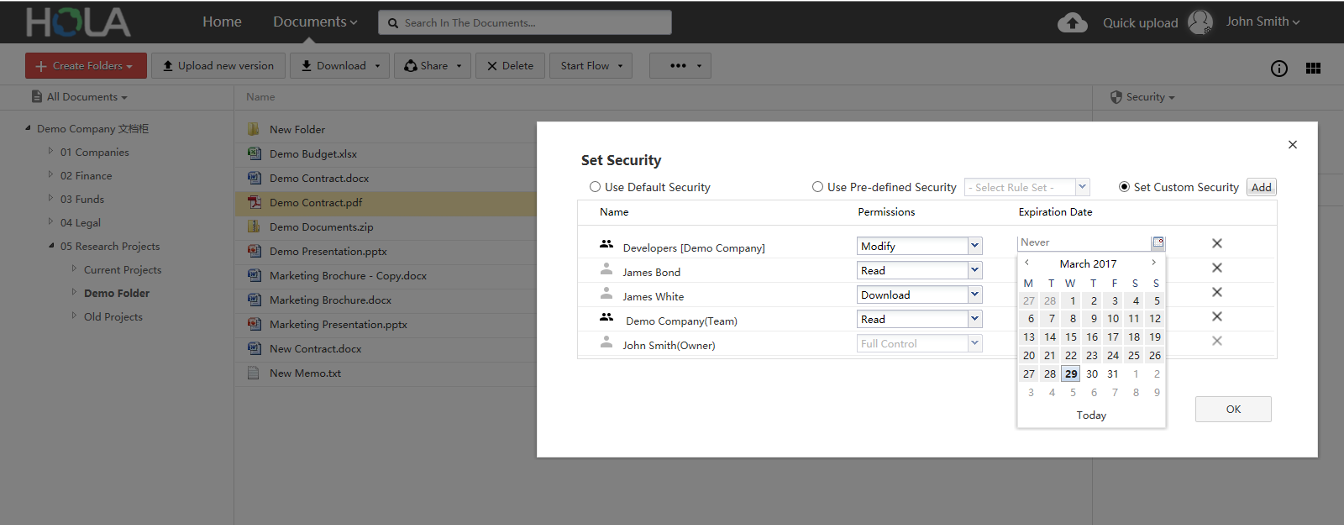
There are times when you want to give to a specific HOLA user only temporary access to certain documents or folders. HOLA provides possibilty to define expiration date on each security setup. Once this expiration date is reached, the user looses temporary access. Obviously, security settings can be changed anytime by users who have proper security privileges.
In this fashion, you can for example grant Read only security privileges for selected document to user John Smith for period of 2 weeks. After 2 weeks, John Smith will loose Read access to selected document.
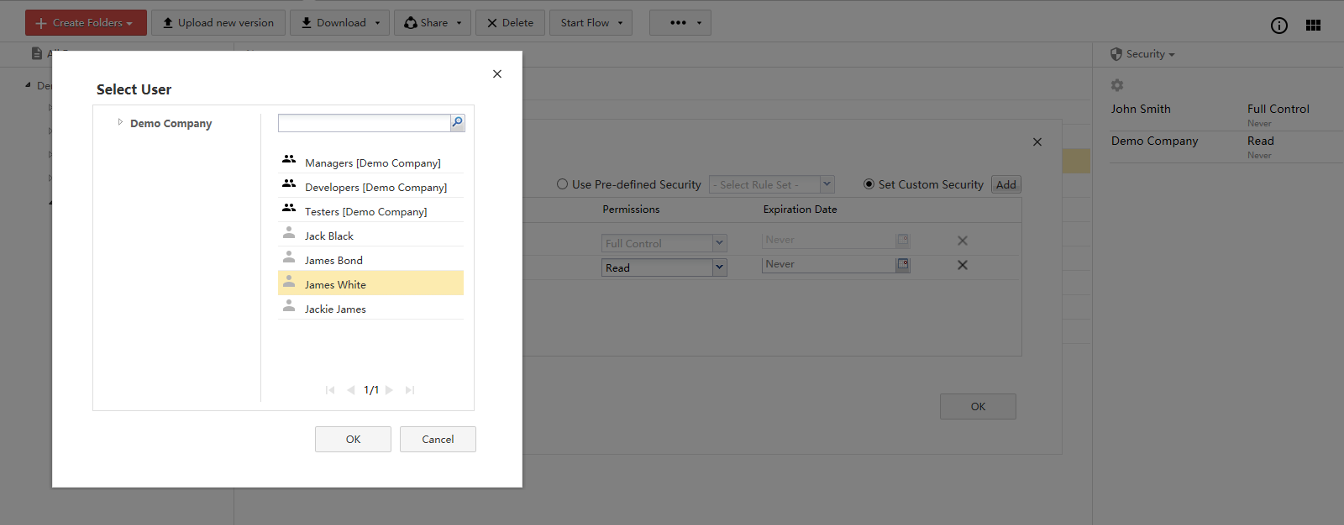
User, Group & and Role based security
Security to documents and folders can be assigned directly to selected users. For example, user John Smith can have Read access to selected document.
HOLA also provides option to create groups (such as Developers, Project Managers, etc.). These groups can contain several users. Document and folder security can be assigned to such groups as well.
You can also create Role (such as Project Controller) as a group with only 1 user.
Advantage of assigned security to Roles and Groups is that if the user is relocated or leaves, it is very easy to re-assign Role or Group, without need to manually remove such user from all security settings.
Public sharing
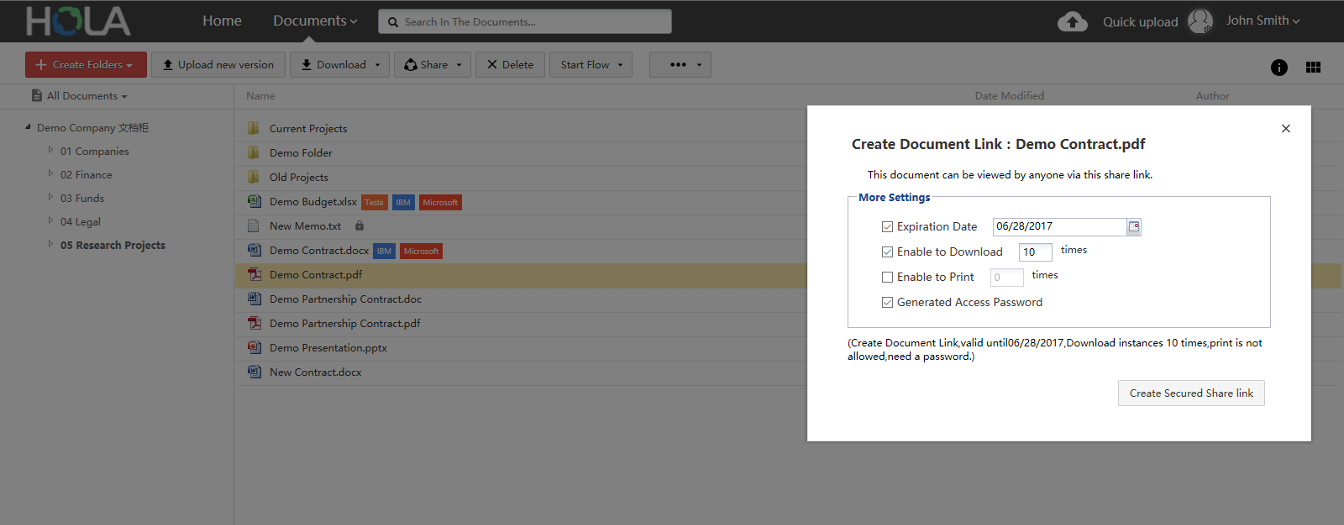
Sometimes you want to provide access to certain document or folder to someone who is not HOLA user. To enable this, HOLA provides feature called Public sharing.
This feature allows user to create a public share link (or QR code) and share such link with people who are not HOLA users (for example your partners, customers or clients). Such people can click on the link and access document or folder.
When setting up public share link, it is possible to specify if shared document or folder should be password protected, how many and what actions public users can do with shared content and when the public share link expires.
Search
When searching for documents & folders in HOLA, the search takes security privileges into consideration. This means that your search results will not contain documents or folders for which you don't have proper security privileges (No Access), even those documents and folders match search terms.
To learn more about how seach works in HOLA, read Search section.
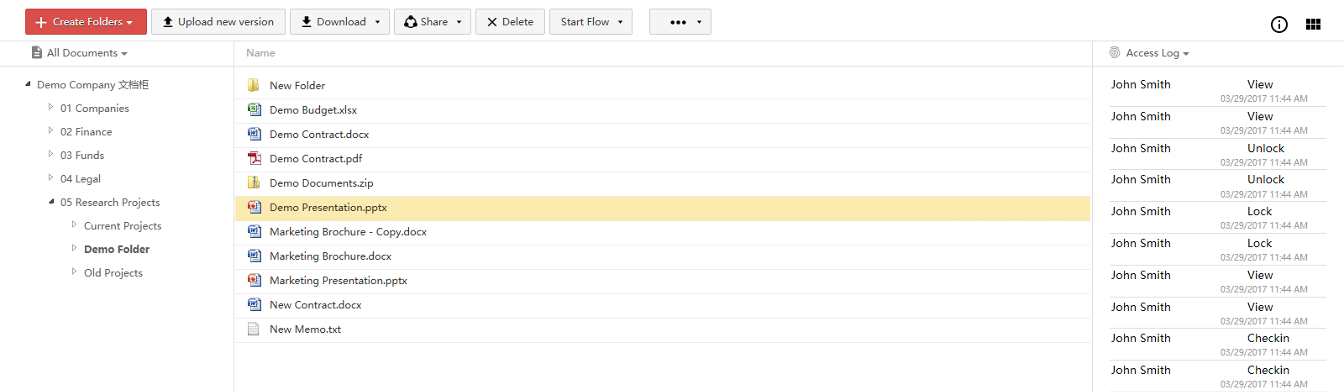
Access log
Every document & folder have their own access log where over 40 possible operations are tracked, together with user name and timestamp.
Secure browsing
All communication between your browser and HOLA is encrypted using SSL. The connection is encrypted with 256-bit encryption and uses TLS 1.0.
SSL stands for Secure Socket Layer. It is a security protocol that provides communication privacy over the Internet. The protocol allows HOLA to securely communicate in a way that is designed to prevent connection eavesdropping, connection tampering or communication forgery. It is same technology used by banks or e-commerce companies to keep your information private and secure during transactions.
Logging-in & logging-out
When you are logging into the HOLA system, outside of username and password you also enter CAPTCHA verification code. This verification code protects HOLA system from brute force login by automatic computer system that tries to guess usernames and passwords and tries to gain access to HOLA system. CAPTCHA verification code can be disabled by HOLA system administrator if necessary.
When you are logged-in into HOLA system through your browser, and you don't perform any actions in HOLA for certain time, your browser session expires and you will get automatically logged-out from HOLA. This prevents other people accessing your HOLA account if you leave your computer and forget to logout from the system.
Backup
HOLA provides tools which enable automatic backup of all documents, document related meta-data as well as search indexes. System administrators have flexibility to configure the backup process so it allows automatic or manual backup of mentioned backup targets individually. For example, administrator can decide to backup only documents, without backing up meta-data and search indexes.